CPAP HACKING VILLAGE
Welcome to the digital frontier
About CPAP Hacking Village
"I'm in this village and I don't like it" -- Gwyddia
Welcome to the CPAP Hacking Village, where we explore the fascinating world of respiratory medical device hardware hacking, reverse engineering, and embedded systems security. Our community focuses on understanding how devices work at the lowest level and discovering vulnerabilities that can lead to innovative security research.
What We Do
- CPAP device reverse engineering and analysis
- Firmware extraction and modification
- Embedded system security assessment
- CPAP device vulnerability research
- Custom hardware development
Talks!
This year's schedule of talks is up. We have some great content to present! Talks will begin at midnight.
Here is this year's schedule:
| Author | Title | Description |
|---|---|---|
| xrqz | I know where you sleep | Modifying a Raspberry Pi RTL-SDR to track locations of cellular-enabled RESMED devices. A discussion of location tracking using easily-obtained commodity hardware. |
| hexalicious | A(H)I and you: using AI to analyze your sleep data. | Using modern AI data analysis techniques to mine interesting insights from your sleep data. |
| xrqz | You snooze you lose! | Assault and (9v)Battery: how to cause harm through the vector of remote update of auto titration configuration settings. |
| hexalicious | The ultimate sleep journal: recording your sleep data on a blockchain.| Examining the pros and cons of storing sleep data on a blockchain. |
|
| xrqz | Securing your sleep | Crypto key generation missteps on sleepy devices. |
| knarphie | Farts are NEVER not funny? CPAP air intakes and humor. | The title says it all. |
| xrqz | Who's got two thumbs and going to take a nap? Analyzing RISC instructions on CPAP device subsystems. | Take a RISC! Come to this talk. |
| hexalicious | CPAP secure boot failures and jailbreaks. | It's the 90s all over again. |
| hexalicious | Awake on the wire: sniffing CPAP traffic sent to provider networks. | Bring your own Wireshark. |
| sigint | Multi-tasking: drink while you sleep. | Alternative uses for CPAP hardware. |
Essential Tools
Every device hacker needs a reliable toolkit. Here are some of the essential tools we use in our research:
Hardware Tools
- Logic Analyzer: For analyzing digital signals and protocols
- Oscilloscope: For examining analog signals and timing
- JTAG/SWD Debugger: For direct chip access and debugging
- Soldering Station: For component modification and replacement
- Multimeter: For basic electrical measurements
Software Tools

Essential tools for CPAP hacking and reverse engineering
Getting Started
Ready to dive into CPAP hacking? Here's a step-by-step guide to get you started:
Step 1: Understanding the Basics
Before diving into hardware hacking, it's essential to understand basic electronics, digital logic, and common communication protocols like UART, SPI, I2C, and USB.
Step 2: Setting Up Your Lab
Create a dedicated workspace with proper lighting, ventilation, and ESD protection. Start with basic tools and gradually expand your collection as you tackle more complex projects.
Step 3: Your First Target
Begin with CPAP devices that have easily accessible documentation.
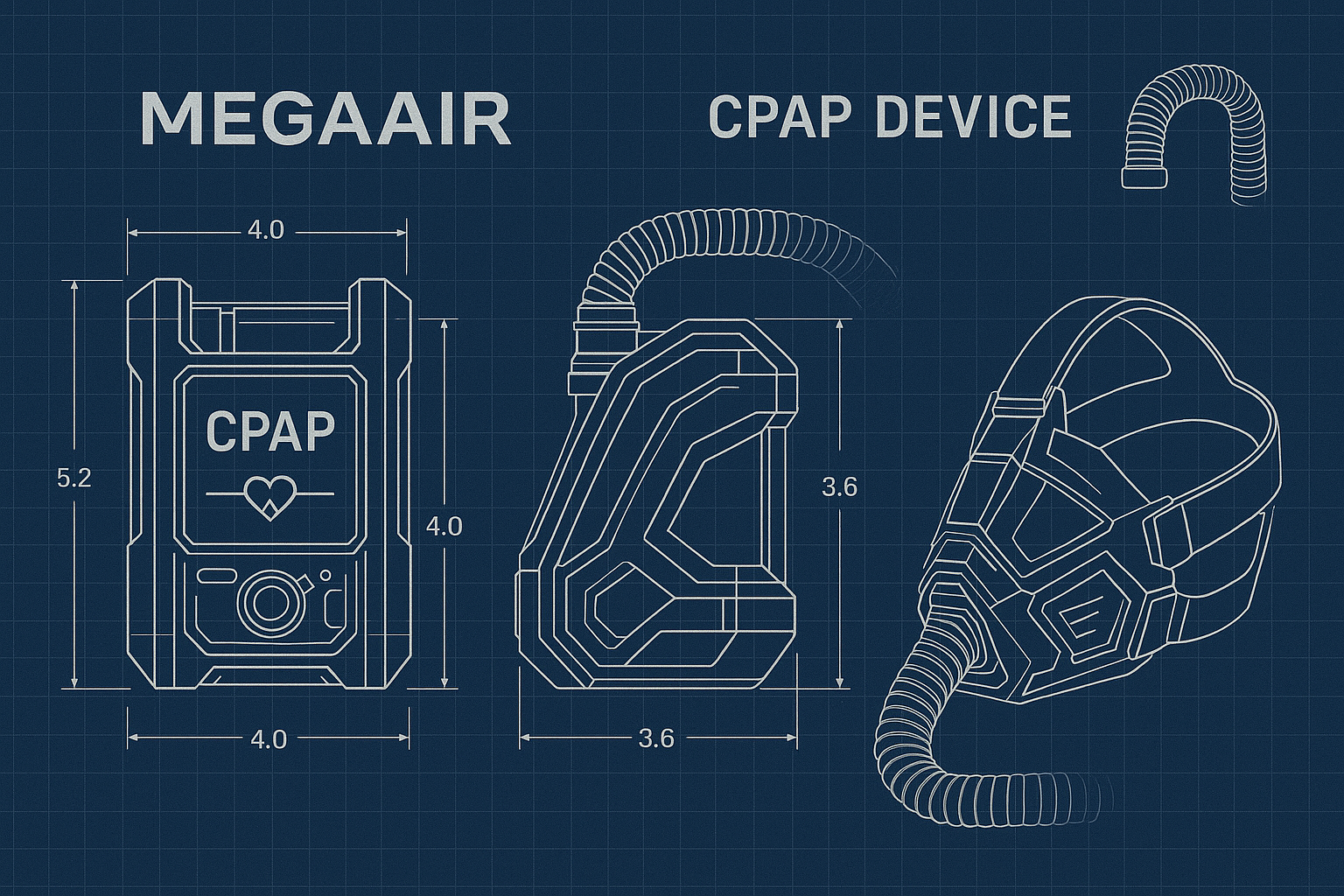
MegaAir CPAP schematics
Project Gallery
Explore some of our community's recent projects and discoveries:

CPAP being reverse engineered

Cyberpunk CPAP mod

The Hoseinator
Join Our Community
Ready to start your device hacking journey? Connect with our community of researchers, hackers, and security enthusiasts.
Remember: Always practice responsible disclosure and only hack devices you own or have explicit permission to test. Our goal is to improve security, not cause harm.